Table of Contents
LDAP (Lightweight Directory Access Protocol)

LDAP is used by The Company on its production servers to authenticate users. Configuration is split into two parts, the LDAP server config and the LDAP client setup.
The previous version of LDAP used dc=oldcompany,dc=com as it's base DN, but the new base DN is dc=int, dc=TheCompany dc=com.
Confusingly, there are two files called ldap.conf on the server (and maybe on other servers too), /etc/ldap.conf is the CLIENT config file, /etc/openldap/ldap.conf is part of the SERVER config in conjunction with /etc/openldap/slapd.conf.
To add users and groups, see Add Users and Groups to LDAP.
Testing Methodology, see page:- Testing LDAP
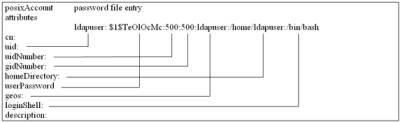
LDAP attributes match /etc/passwd fields according to the illustration below:-
LDAP Server Config
LDAP is not used for authentication on inet03/04 to prevent lockouts. Hence local accounts are needed for users. Use useradd to create them.
useradd -d /home/user123 -g noc -s /bin/bash -c "MyUser 123" -m user123
TLS encryption is used in preference to SSL because TLS encryption uses the standard unencrypted LDAP port, SSL needs another port opening which would require firewall rules creating.
TLS encryption is started automatically if the client is configured to use it, ldap log files look like:-
Jun 16 13:01:40 inet03 slapd[28776]: conn=84 op=0 STARTTLS Jun 16 13:01:40 inet03 slapd[28776]: conn=84 op=0 RESULT oid= err=0 text= Jun 16 13:01:40 inet03 slapd[28776]: conn=84 fd=23 TLS established tls_ssf=128 ssf=128
Background Reading
http://www.syntaxtechnology.com/2009/09/openldap-on-centos-5-3-x86_64-part-1/
Secure Centralised Logins With Fedora, OpenLDAP and TLS
Local info
The master LDAP server is inet03, all updates should be carried on on this server.
Config
[root@inet03 openldap]# pwd /etc/openldap [root@inet03 openldap]# ls -l total 28 drwxr-xr-x 2 root root 4096 Jul 2 2008 cacerts <----- Certificate Directory -rw-r--r-- 1 root root 330 Nov 26 2008 ldap.conf <----- Client Config file drwxr-xr-x 3 root root 4096 Jan 5 2009 schema <----- Schema files describing object classes -rw-r----- 1 root ldap 3930 Nov 24 09:50 slapd.conf <----- Server Config file
Logging is set to use syslog and syslog.conf directs openLDAP logs to /etc/openldap/openldap.log. By default, this log file is not rotated with logrotate. Ther verbosity of the logging is controlled by a number in the config file which is made up of logging levels added together, see OpenLDAP logging levels.
In slapd.conf, add some logging directives,
logfile /var/log/openldap/openldap.log loglevel 256 #loglevel -1
Logging seems to be via syslog even with a logfile line, so we need to specify where logging actually goes, in /etc/syslog.conf add these to the bottom and restart syslog. The path to the filename must exist so mkdir it if it doesn't:-
#openldap local4.* -/var/log/openldap/openldap.log
Secure SSL LDAP access
Secure operation with TLS or ssl relies on a correct server certificate being available and some lines in slapd.conf.
TLSCACertificateFile /etc/openldap/certs/inticacert.pem TLSCertificateFile /etc/openldap/certs/inet03.ldap-cert.pem TLSCertificateKeyFile /etc/openldap/certs/inet03.ldap.key TLSVerifyUser never TLSVerifyClient allow TLSCipherSuite HIGH:MEDIUM:-SSLv2
SSL certs live in /etc/openldap/certs/ and are issued to inet03/4.prod.int.TheCompany.com. The directory should look like this:-
[root@inet03 certs]# tree -L 2 /etc/openldap/certs/ /etc/openldap/certs/ |-- inet03.ldap-cert.pem |-- inet03.ldap-csr.pem |-- inet03.ldap.key |-- Thecompany-cacert.pem |-- ldap-client-cert.pem
Creating ssl CSR and Key.
[root@inet04 certs]# openssl genrsa -out inet04.gyprod.int.TheCompany.com.key 2048 Generating RSA private key, 2048 bit long modulus ...............................+++ ...................................................+++ e is 65537 (0x10001) [root@inet04 certs]# openssl req -new -key inet04.gyprod.int.TheCompany.com.key -out inet04.gyprod.int.TheCompany.com-csr.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [GB]:GG State or Province Name (full name) [Berkshire]:Guernsey Locality Name (eg, city) [Newbury]:Guernsey Organization Name (eg, company) [My Company Ltd]:The Company Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:inet04.gyprod.int.TheCompany.com Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Secure vs non-secure operation
The operation of the secure and non-secure servers is controlled by a file in /etc/sysconfig:-
[root@inet03 sysconfig]# cat /etc/sysconfig/ldap # Parameters to ulimit called right before starting slapd # - use this to change system limits for slapd ULIMIT_SETTINGS= # How long to wait between sending slapd TERM and KILL # signals when stopping slapd by init script # - format is the same as used when calling sleep STOP_DELAY=3s # By default only listening on ldap:/// is turned on. # If you want to change listening options for slapd, # set following three variables to yes or no SLAPD_LDAP=yes SLAPD_LDAPS=yes SLAPD_LDAPI=no
The SLAPD_LDAPS was set to yes to enable SSL access, but this is not required for TLS as TLS uses an insecure channel and negotiates a secure connection over it. This is the same way that TLS works with SMTP email.
Start the daemon with service ldap start, check for listening connections with:-
[root@inet03 certs]# netstat -lt | grep ldap tcp 0 0 *:ldap *:* LISTEN tcp 0 0 *:ldaps *:* LISTEN tcp 0 0 *:ldap *:* LISTEN tcp 0 0 *:ldaps *:* LISTEN
Test Config file syntax:-
[root@inet03 certs]# slaptest config file testing succeeded
Errors
Replication
inet03 has a replica on inet04. Replicas will need to be help on inet01 and inet02 in xxx.
In LDAP-speak, inet03 is a provider, whilst inet04 is a consumer. All replication is done using syncrepl, slurpd is not used at all.
inet04 acts as a consumer and replicates its LDAP data base from the provider server, net03, the config for this is in /etc/openldap/slapd.conf at the bottom:-
syncrepl rid=123
provider=ldap://inet03.gyprod.int.igt.com:389
type=refreshOnly
interval=00:00:01:00
searchbase="dc=int,dc=TheCompany,dc=com"
scope=sub
schemachecking=off
updatedn="cn=Manager,dc=int,dc=TheCompany,dc=com"
bindmethod=simple
binddn="cn=Manager,dc=xxxxxxx"
credentials=****password***secret
Testing Access
ldapsearch -x -W -D 'cn=Manager,dc=int, dc=TheCompany, dc=com' -b "" -s base -h inet03 -x Simple Auth, not SASL -W Prompt for simple Auth, not on command line -D Distinguished name to bind with -b search Base -s Scope of search, base, onelevel or subtree. -h Host to search on -S attr, sort the results by attribute 'attr' (see below) eg. to see all users and UID's:- ldapsearch -x -W -D 'uid=astringer,ou=People,dc=TheCompany, dc=com' -b 'ou=People,dc=TheCompany, dc=com' -s onelevel | grep -E 'cn:|uidN|# ' eg. to see just one user:- ldapsearch -x -W -D 'uid=astringer,ou=People,dc=int, dc=TheCompany, dc=com' -b 'cn=testuser,ou=People,dc=int, dc=TheCompany, dc=com' -s base eg. to get email address for one user:- ldapsearch -x -W -D 'uid=astringer,ou=People,dc=int, dc=TheCompany, dc=com' -b 'cn=testuser,ou=People,dc=int, dc=TheCompany, dc=com' -s base mail Enter LDAP Password: # extended LDIF # # LDAPv3 # base <cn=testuser,ou=People,dc=prod,dc=wagerware,dc=net> with scope base # filter: (objectclass=*) # requesting: mail # # testuser, People, prod.wagerware.net dn: cn=testuser,ou=People,dc=int, dc=TheCompany, dc=com mail: test.user@TheCompany.com # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
use -L or -LLL to reduce the “clutter” returned and just leave the query result.
Sorting attributes, can produce oddities, sort by gidNumber below returns the gid value sorted by first digit, not whole value:-
ldapsearch -x -W -D 'uid=astringer,ou=People,dc=prod, dc=product, dc=net' -b 'ou=Group,dc=prod, dc=product, dc=net' -S gidNumber -s sub cn gidNumber ...edited... cn: codebldr gidNumber: 2046 cn: technicalops gidNumber: 205 cn: TechnicalOpsGIB gidNumber: 205
To get attributes eg. uid where you know a different attribute, eg. cn:-
[root@inet01 ~]# ldapsearch -h inet01 -x -W -D 'cn=Manager,dc=product,dc=net' "(cn=Usrname Desiraj)" uid userPassword uidNumber Enter LDAP Password: # extended LDIF # # LDAPv3 # base <> with scope sub # filter: (cn=Username Desiraj) # requesting: uid userPassword uidNumber # # Username Desiraj, People, prod.product.net dn: cn=username Desiraj,ou=People,dc=prod,dc=product,dc=net userPassword:: e01ENX1UV2U4ZTBBM2tjYzRHR29kam9MSXFBPT0= uidNumber: 8857 uid: username23 # search result search: 2 result: 0 Success # numResponses: 2 # numEntries: 1
Web Access
Client Side setup
Several files need editing to enable ldap access, lines or blocks of directives which require changing are shown below, lines which are left alone are not shown for clarity:-
[root@inet03 pam.d]# more /etc/ldap.conf # This is the configuration file for the LDAP nameservice # switch library and the LDAP PAM module. # host inet02 inet01 # The distinguished name of the search base. #base dc=example,dc=com base dc=prod,dc=product,dc=net
[root@inet03 pam.d]# more /etc/nsswitch.conf # # /etc/nsswitch.conf passwd: files ldap shadow: files ldap group: files ldap #hosts: db files nisplus nis dns hosts: files dns ethers: files netmasks: files networks: files protocols: files ldap rpc: files services: files ldap netgroup: files ldap publickey: nisplus automount: files ldap aliases: files
[root@inet03 pam.d]# cat /etc/openldap/ldap.conf #BASE dc=example, dc=com #URI ldap://ldap.example.com ldap://ldap-master.example.com:666 #SIZELIMIT 12 #TIMELIMIT 15 #DEREF never #URI ldap://127.0.0.1/ URI ldap://inet02 ldap://inet01 #BASE dc=example,dc=com BASE dc=prod,dc=product,dc=net TLS_CACERTDIR /etc/openldap/cacerts [root@inet03 pam.d]#
For TLS operation, the root CAcerts file must be copied to TLS_CACERTDIR, as above.
Add the pam module to /etc/pam.d/sshd to auto create home directories:-
[root@inet03 pam.d]# cat sshd #%PAM-1.0 auth include system-auth account required pam_nologin.so account include system-auth password include system-auth session optional pam_keyinit.so force revoke session include system-auth session required pam_mkhomedir.so skel=/etc/skel/ umask=0077 session required pam_loginuid.so
Also you can add this line to a pam file like /etc/pam.d/sshd:-
account required pam_access.so accessfile=/etc/security/access-login.conf
Users must additionally be listed in /etc/security/access-login.conf to allow logins.
Test LDAP access with ldapsearch -x.
Backups
In /root/scripts there is a bash script which dumps the LDAP database to LDIF. A separate script on noc01 copies this data base to BigCity for off-site storage.