Table of Contents
Web-based Certificate Authority
This is a project of mine I started in approx 2007, it aims to give a “Self - Service” approach to creating SSL certificates via a web browser based interface.
It is intended to be used inside an organisation where certificates are required to be issued against an internal CA.
By creating a two step process (upload a certificate signing request and sign the CSR with a bash based wrapper to openssl) some measure of authentication against a request can be done, maybe this is just as simple as a phone call or email to the person requesting the certificate.
No in-depth checks are performed such as a commercial CA would (hopefully) do to justify their fees, but this project is aimed at a different market.
The code for this is hosted on Github:- https://github.com/andrewjstringer/EnterpriseWebCA
Background
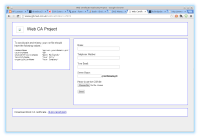 This project was started to implement a web based self-service for generating SSL certificates. It is intended for use within a company rather for the use of the public.
This project was started to implement a web based self-service for generating SSL certificates. It is intended for use within a company rather for the use of the public.
At the time, I was trying to promote use of org signed ssl certs tied to the implementation of a new internal DNS name and rollout. Up to this point, self signed ssl certs were used as there was no mechanism to produce internal ssl certs. Trying to automate this seemed the best way to ease use and deployment.
A Self-Signed CA root certificate is created (or imported) and submitted CSR's are signed by this root. The Self-Signed CA root should be imported in to all browsers or other devices which would access an SSL based service signed by this root.
The web backend is written in PERL and runs as cgi-bin scripts with .shtml files as templates. The approval backend is written in BASH.
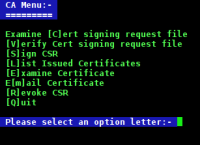 The backend is written as a bash shell script and is menu driven. ./menu.sh will start this off. As it should be run as root, no authentication is performed as this should have already been done by logging in. However, the root CA certificate should be password protected, and without this password, it is impossible to sign a certificate.
The backend is written as a bash shell script and is menu driven. ./menu.sh will start this off. As it should be run as root, no authentication is performed as this should have already been done by logging in. However, the root CA certificate should be password protected, and without this password, it is impossible to sign a certificate.

sudo to run this, apart from access to ssl, it doesn't really require root. By setting permissions. it should be possible to run it as a regular user.
To Do
- Signing backend in BASH to be configured to run as regular user, not root.
- Certificate revocation List and mechanism to manage it should be written.
- Signing certs could be done through a web front end, at the time it was easier to write the front end without requiring any authentication, and using BASH for the back end would require an admin to use ssh to login, thereby adding authentication to the issuing process.
- openssl commands are shelled out, probably better to try to use language native modules to do this work.
- Create a separate root CA certificate and then create an intermediate CA cert to use for actual signing.
This would allow implementing a new intermediate or revoking and intermediate if compromised without forcing users to have to import a new CA root.
- Maybe just for fun…. rewrite using Python!
Code
The code is split in to three basic sections.
- Web based front end for users to submit CSR's to, this is written in Perl.
- Bash based back end for administrators to verify the request, sign the CSR and email a certificate to the user requsting it.
- Apache code to set up virtual host Apache enable site - from Ubuntu sites-available dir
Structure
The code lives under /opt/webca/:-
.
├── openssl
│ ├── certs
│ │ ├── xxxx.cert
│ │ ├── yyyy.cert
│ │ └── zzzz.cert
│ ├── crl
│ ├── crlnumber
│ ├── index.txt
│ ├── index.txt.attr
│ ├── index.txt.attr.old
│ ├── index.txt.old
│ ├── newcerts
│ │ ├── 1000.pem
│ │ ├── 1001.pem
│ │ ├── 1002.pem
│ │ └── 1003.pem
│ ├── openssl.cnf
│ ├── private
│ │ ├── aaaa-ca.cert.pem
│ │ ├── aaaa-ca.key.pem
│ │ └── README-key.txt
│ ├── serial
│ └── serial.old
├── processroot
│ ├── emaillist.txt
│ ├── mailbody.txt
│ ├── menu.sh
│ ├── test
│ │ ├── decodecsr.pl
│ │ ├── mailtest.sh
│ │ ├── sign.sh
│ │ └── verify.sh
│ └── webuploads
│ ├── aaaa.cert
│ ├── bbbb.csr
│ └── cccc.csr
└── webroot
├── cgi-bin
│ └── csrupload.pl
├── https
│ ├── csr-upload.html
│ ├── zzzz-int-ca.cert.crt
│ ├── index.html
│ ├── index-old.shtml
│ ├── info.html
│ ├── webca.png
│ └── webca-screen.css
├── logs
│ ├── webCA-access.log
│ └── webCA-error.log
└── webca-data